We begin by gathering detailed information about the target system’s structure, network setup, and software components, which helps identify potential vulnerabilities. At the same time, obtaining proper authorization from the client is crucial to ensure the process remains legally and ethically sound. This initial phase typically lasts about a week and sets the stage for the next steps.
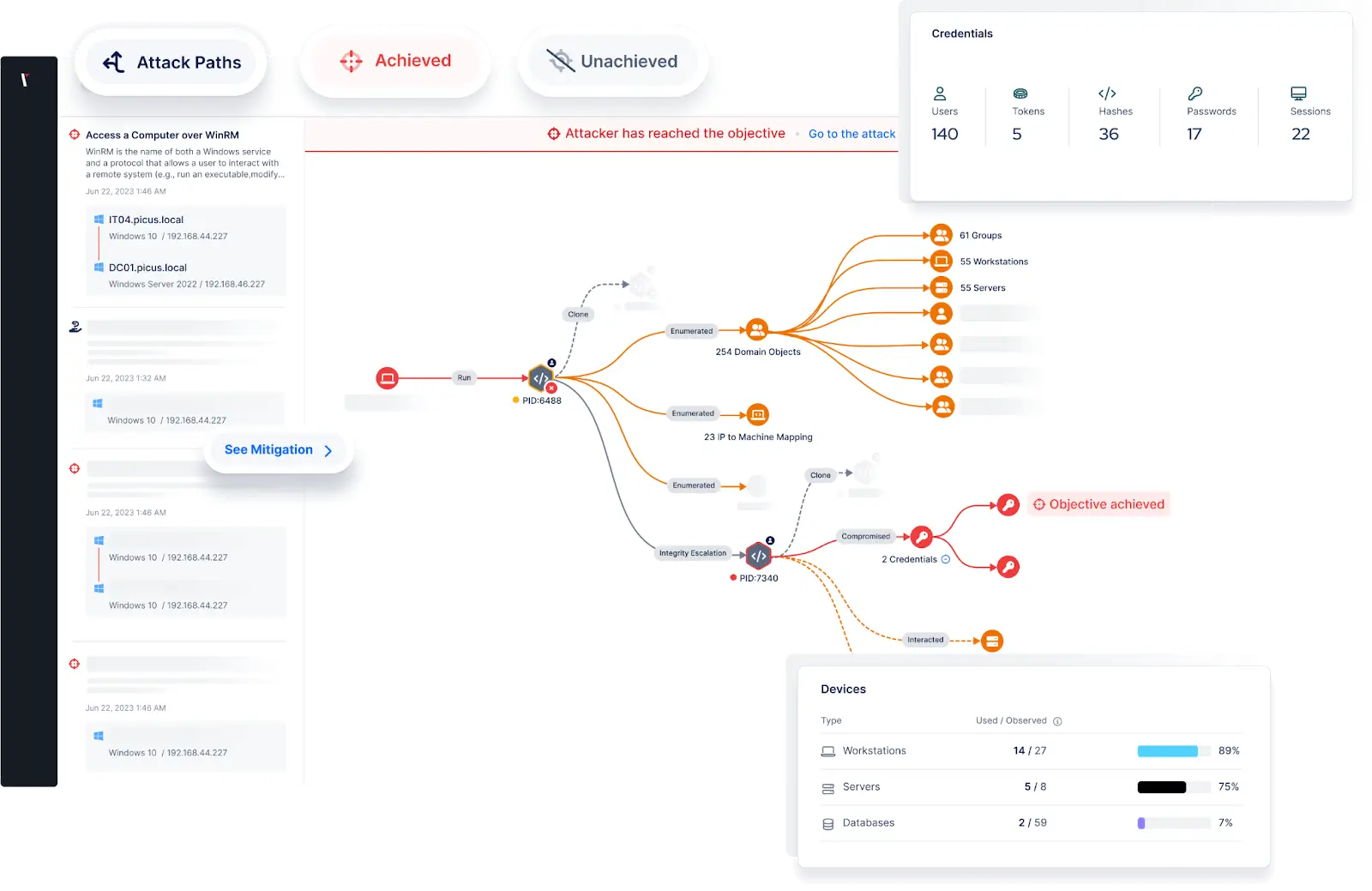
Providing pen testing services, we conduct controlled simulations of various attack scenarios to uncover vulnerabilities. Our security testing specialists explore system layers, including applications, networks, and user access controls. By mimicking real-world threats, the team reveals hidden flaws that automated tools might miss. The duration of this phase, ranging from one to three weeks, depends on the system's complexity. This step's thoroughness is key to identifying even the most intricate vulnerabilities.